The introduction of MFA also affects connection with SSH to CSCS systems. It is no longer possible to authenticate with a username/password and user-created SSH keys: it is necessary to use a certified SSH key created by a CSCS SSHService. Keys are valid for 24 h, after which a new key must be generated through our SSHService GUI or by using a command-line script.
The number of certified SSH keys is limited to 5 per day. Once you have reached this number you will not be able to generate new keys until at least one of these key expires or keys are revoked (see the corresponding FAQ on the User Portal).
This involves the steps explained in the instructions below.
Step-1. Obtaining the certified SSH keys using either of the following ways:
(Option-1) Using Web-based SSHService
a. Access the SSHService web application by accessing the URL, https://sshservice.cscs.ch
b. Follow the authentication instructions.
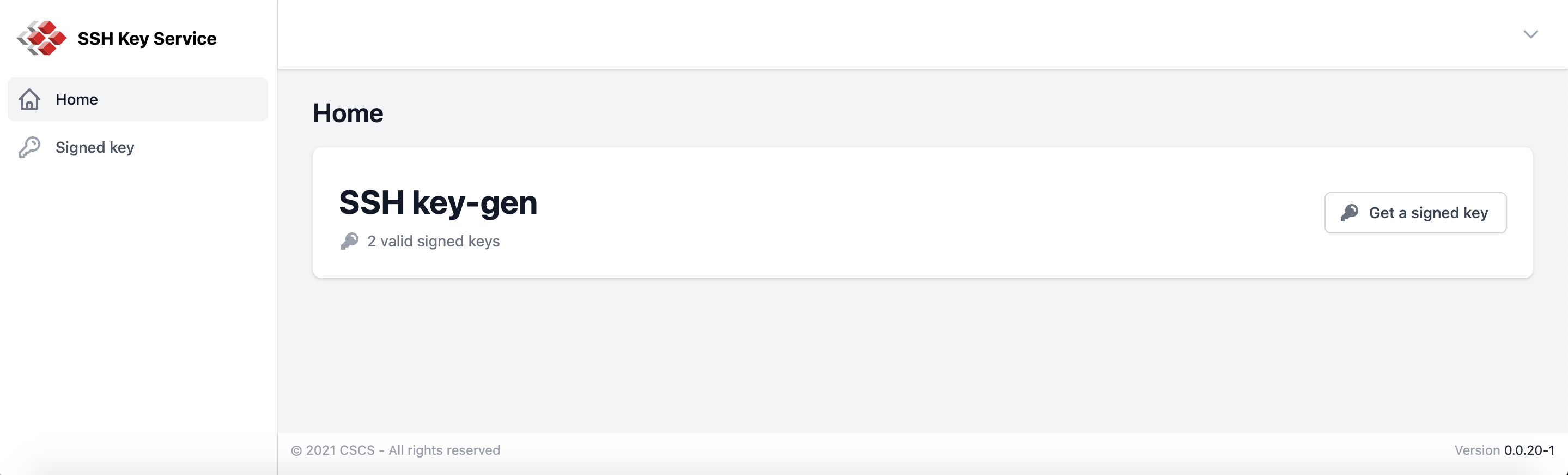
c. Select "Signed key" on the left tab and click on "Get a signed key"
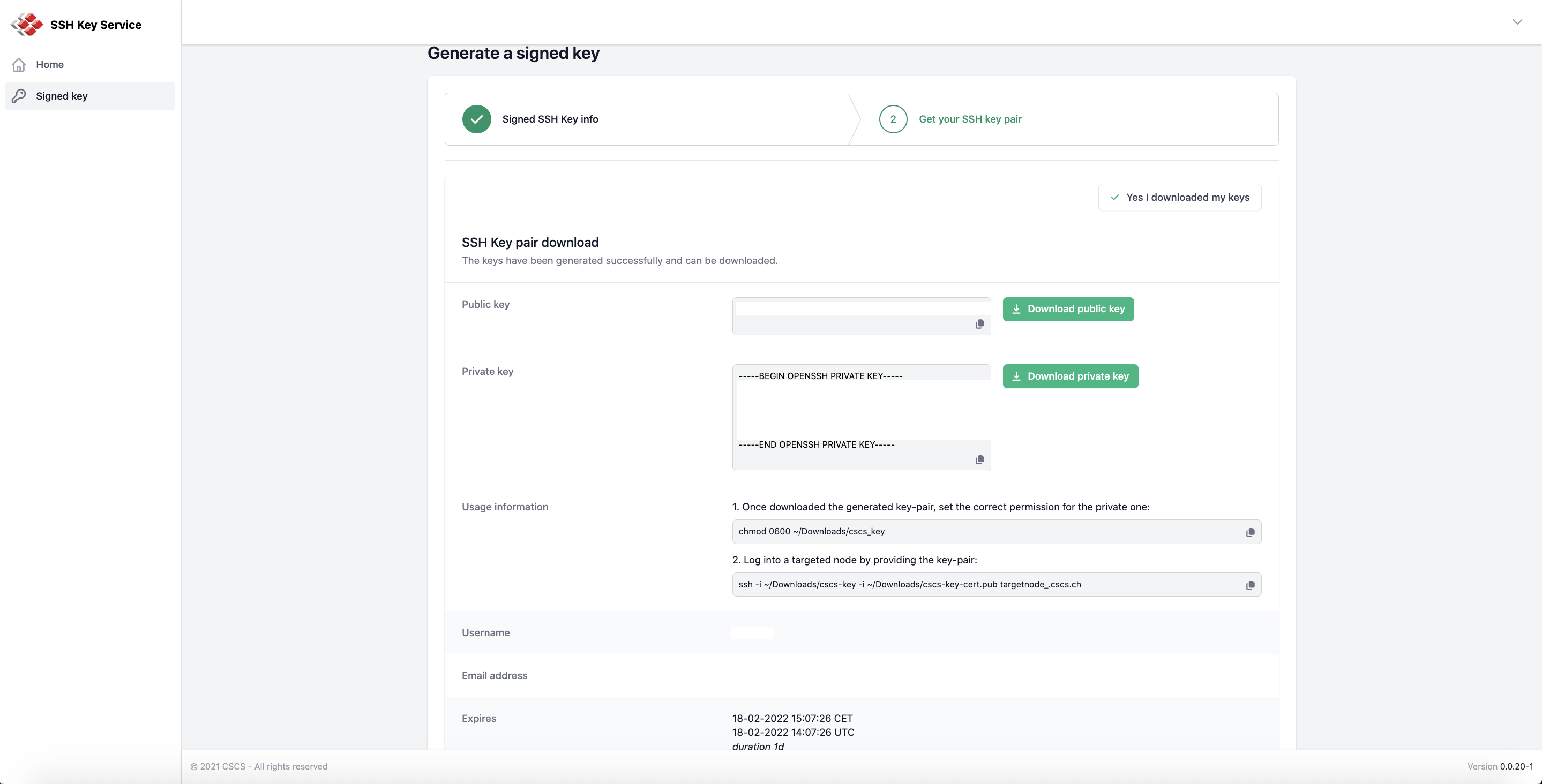
d. On the next page a key pair is generated and ready to be downloaded. Download or copy/paste both keys.
Creating and downloading signed keys
e. Setup the keys on your local machine:
mv /download/location/cscs-key-cert.pub ~/.ssh/cscs-key-cert.pub mv /download/location/cscs-key ~/.ssh/cscs-key chmod 0600 ~/.ssh/cscs-key
(Option-2) Using SSHService Command-line
On Linux and MacOS, the SSH keys can be generated and automatically installed using a command-line script. This script is provided in pure Bash and in Python. Python 3 is required together with packages listed in the file requirements.txt provided with the scripts. We recommend to use a virtual environment for Python.
a. Obtain the scripts by cloning the following repository:
git clone https://github.com/eth-cscs/sshservice-cli
b. Execute either the Bash script or Python script as shown below:
Bash version:
./sshservice-cli/cscs-keygen.sh
Python version:
python -m venv mfa cd mfa source bin/activate git clone https://github.com/eth-cscs/sshservice-cli cd sshservice-cli pip install -r requirements.txt python cscs-keygen.py
The above in Python version is for one off only and from then onwards to generate/download the keys use the below commands,
source mfa/bin/activate cd mfa/sshservice-cli python cscs-keygen.py
c. Follow the interactive script and download the key pair by providing the authentication information (username, password, OTP). Please note the script generates the key pair inside the .ssh directory of your local home folder:
ls -latr ~/.ssh/
Step-2. Accessing CSCS systems using the certified SSH keys
Please follow the below options on Linux or MacOS,
i. Setup a passphrase on the private key using the following,
ssh-keygen -f ~/.ssh/cscs-key -p
ii. Add the key to the SSH agent (Make sure ssh agent is up & running or else please execute eval $(ssh-agent)),
ssh-add -t 1d ~/.ssh/cscs-key
iii. Connect to the login node 'ela', using the following ssh command
ssh -A cscs_username@ela.cscs.ch
iv. Jump to cluster from ela using the following command
ssh <dom> or <daint> or <etc...>
Frequently encountered Login errors
1. If you see the message "Too many authentication failures" you may have too many keys in your ssh agent. You should remove the unused keys from the agent or flush them all with the following command:
ssh-add -D
2. If a user is attempting to access CSCS systems with SSH using an expired key, then SSH will fail with an error message as follows:
Permission denied ...
The validity of the key can be checked with the command
3. If you see the message "Could not open a connection to your authentication agent" while adding the keys to your agent, Please make sure the agent is up, and if not bring up the agent using the following command,eval $(ssh-agent)
ssh-keygen -L -f ~/.ssh/cscs-key-cert.pub
Type: ssh-ed25519-cert-v01@openssh.com user certificate
Public key: ED25519-CERT SHA256:pF3znTpw2EyGkjeCLnhXqGjf0Ar0RXcomyVN+kxmZmI
Signing CA: ED25519 SHA256:BwybyU6cNJBS7AX6BdwgJV2emGDV4lkKY4413WRGboY (using ssh-ed25519)
Key ID: "username"
Serial: 0
Valid: from 2021-09-30T09:31:26 to 2021-10-02T09:31:26 <= this line shows the validity
Principals:
username
Critical Options: (none)
Extensions:
permit-X11-forwarding
permit-agent-forwarding
permit-port-forwarding
permit-pty
permit-user-rc
Using MFA on a Windows system
The instructions in the previous sections focused on users working with Linux/Mac OS. Windows users can find a short guide MFA with Windows, describing tested workflows and tools compatible with CSCS MFA.
Artifacts from the Webinar on Multi Factor Authentication & SSH Key Service at CSCS
For the users who missed our webinar on Dec 5th, 2022 we provide the video recording here.
The powerpoint which we presented to the audience in the webinar on Dec 5th, 2022 is attached here for reference to users.
Also attaching here the pdf with the questions we gathered from the webinar along with CSCS responses.
Process for requesting a long term key (Deprecating)
- Please open a ticket in case if you already hold a service account that is performing automation on your application side which needs a long term key.
- Please open a ticket if you need a key pair that is valid for 7 days and if you are running workflows using some sort of automation tools/scripts.
Notes: We are encouraging users to migrate to FirecREST for submitting jobs through automation workflows. Meanwhile users porting their workflows to FirecREST we still support users with the Long term keys and 7 days key.
Reset OTP or register a new device/authenticator app
- Please follow this procedure to reset OTP